←All Posts Posted on September 24, 2014 By admin
We have all heard of encryption, but what does this term actually signify? To answer this question, we must first delve into the definition of encryption and appreciate the ways in which it operates. At Elvidence, we often have to deal with encryption so we think that it is important to clear up a few main points. When we investigate a system, we often find that data has been compromised because of buggy software, a weak password or through another channel. Or, during the Investigation we need to “crack” the encryption used by another party to gain access to certain information.
The Basics
Let us imagine that 101010 is our message. A random number such as 100001 (the key) is generated and a separate algorithm is used to combine these two numbers into a cipher text. If we use an algorithm known as XOR (exclusive OR), our message (101010) combined with the key (100001) turns into 001011 (the end cipher text). This is an example of what is known as a symmetric key encryption.
It is interesting to note that symmetric key ciphers were used well before the computer. An example of a strong symmetrical cipher is seen in the “one-time” pads and the associated numbers stations that were used extensively by NATO and the Warsaw Pact during the Cold War. This encryption technique is unbreakable if three rules are followed:
The only problem arises form the fact that a new one-time pad will be needed at some stage. This is where Diffie-Hellman algorithm comes in handy. Their algorithm solves the issue of a key exchange via mathematical principle similar to 1 + 2 = 3 or 1 + (1+1) = 3. This example is rather oversimplified but the concept is similar. We will look at this shortly.
On the other hand, an asymmetrical system employs two different keys which are mathematically related, but independent of one another. To put it simply, a symmetrical system uses two groups of digits (the message and the key) to arrive at the third cipher. An asymmetrical system uses three groups (as the “key” is split into two groups (key + key + message) ).
A Look at Two Common Key-Exchange Algorithms
The Diffie-Hellman Key Agreement algorithm was invented by three scientists and is famed for its seamless integration, its bespoke simplicity and overall elegance. This “bare bones” nature has enabled the algorithm to be widely accepted in many circles. A second type is known as the RSA Key Exchange Process. Both of these are explained in further detail by Matthieu Deru in a post entitled “RSA Dillie-Hoffman Explained in Three Minutes“.
As technology continued to evolve, it was not long before stronger methods were needed. This notion was espoused in a 1976 article which was published in the Journal of IIEE Transactions on Information Theory in a piece titled “New Directions in Cryptography“. This was the first time when asymmetrical key encryption was introduced to the global community and the paper impacted the ways in which we currently use this technology.
A Changing World
As the interconnected nature of computing systems continues to grow, the need for high levels of security must be addressed at an even faster pace. Unfortunately, this metric still lags behind other facets of communications and technology. While ecliptic curves and quantum maths are indeed making headway, human error and implementation techniques can cause problems.
Symmetric Key Encryption
This method is typically used for encrypting files and computer disks. There are five categories that should be understood in greater detail.
Direct substitution shift method uses a cipher to transform data within a text, however it does not remove or hide the frequencies of characters. So, a frequency analysis could be used to crack the code (for instance, noting every time that an “e” is replaced with a “c” within a text). Thus, more alphabet tables alongside random sequencing is added.
Shift ciphers employ mathematical formulas to literally shift and modify the value of a number (think of a clock which reads from one to twelve; the number thirteen is translated back to one). This can also be vulnerable to frequency analysis.
A permutation cipher will modify the parts of a message but yet its total character count and frequency will remain the same. Note that this method along with the previous ones all rely upon the manipulation of a single character.
To combat this, a block cipher will literally assign characters into blocks and then encrypt the entire block. Examples are AES, DES and Triple DES.
A stream cypher encrypts every single piece (bit) of data with a random cipher value. This method was previously used in WEP wireless protocol but it is now considered to be insecure. It is insecure because of the way it was implemented into the wireless protocol. The cipher itself (RC4) remains strong, secure and unbroken. This illustrates an important problem with implementation; combined with human and hardware vulnerability, such instances can cause problems with even the strongest levels of encryption.
Shortcomings of the Encryption Solutions
We must appreciate the many shortcomings arise from quality control regarding the source code, implementation problems (as seen in the RC4 example above) and the vulnerability of an existing operating system and computer hardware. Other causes can include:
Bad passwords, social engineering attacks and malware are additional threats that are difficult to address.
To review, security systems call under four main categories:
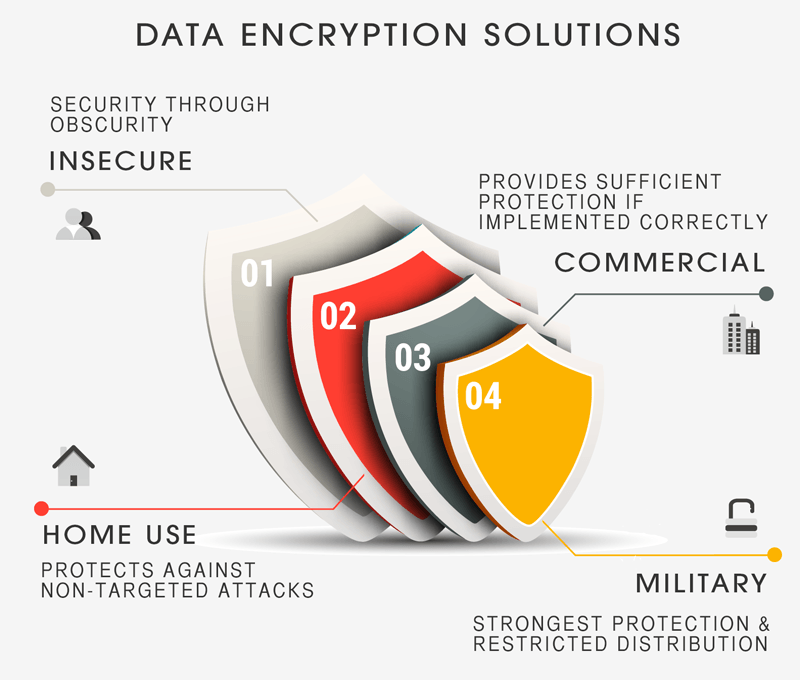
At Elvidence, we appreciate the immutable fact that the encryption technology of today may not work tomorrow. We are information security and computer forensic investigators. Our duty is to inform our customers that encryption alone is insufficient for data security. We help clients choose the best products (based around their needs) and we have the technical know-how to appreciate the vulnerabilities of each system and the best methods used to protect the data in question. As modern encryption continues to evolve, so will our methods and recommendations.