←All Posts Posted on October 3, 2014 By admin
Information security is no laughing matter. Several recent incidents clearly demonstrate the damage that an information security breach can cause to a company’s brand and reputation. This article discusses the application of eDiscovery and Computer Forensics methods to help lessen the risk of your data falling into the wrong hands. To address this issue correctly, we must first distinguish the differences between Data Loss Prevention and Data Leak Prevention (DLP). Data loss occurs when data is leaked and falls into the hands of another party (such as a hacker or your competition). On the contrary, a leak can be defined as when control of data is lost although it still has not been accessed by a malicious party. Still, such a loss of control may eventually lead to the loss of this information entirely. So, we will use the acronym DLP interchangeably when referring to either event.
We can break the focus of DLP down into the monitoring of data in three different states. These are:
For DLP to be effective, all information within the organisation needs to be classified according to its sensitivity (secret, sensitive, internal or public). This enables the DLP software to effectively monitor all necessary metrics and “flag” suspicious activity.
Business leaders are less worried about DLP technology and methods. Instead they are concerned with how information is being viewed and handled by internal employees, third-party contractors and how well this information is protected from hackers. Regulatory risks are also increasing. Regulators have renewed their focus on data protection requirements, breach notification rules and introduced significant enforcement penalties. In practise, we have noted that less than thirty per cent of businesses employ a document classification system. Even less have implemented any type of control framework due to the prohibitive cost and effort in regards to DLP management. DLP is complex, expensive to implement, and most likely to be deployed in large regulated corporations and those organisations with secrets to protect.
While the challenges are profound, the advances in Electronic Discovery (or eDiscovery) have enabled DLP efforts to be complimented with analytical power used in computer investigations. In essence, eDiscovery is primarily used in civil litigations and it focuses upon the identification and intelligent processing of relevant documents or topics within large volumes of unstructured data. While DLP can be the “broadsword”, eDiscovery can be seen as the “scalpel”.
Electronic Discovery offers advanced data analytics methods to discover past, present and potential data leaks. An example of this can be the use of similar document identification technology, the ability to identify drafts, revisions and communications, which relate to the chosen topic in question. When dealing with large amounts of data, grouping files in different formats (PDF, DOC, TXT, EML, MSG) containing similar text is a powerful way to locate relevant, sensitive information and skip whole groups of documents that aren’t relevant. Computer forensic techniques can be used to dig further to identify: who, when, where and how the information leaked out. Essentially, a dedicated DLP solution represents a control system in place, however it is difficult and expensive to deploy or maintain.
An eDiscovery approach to DLP initially focuses on email, because it is the most likely vector of data leakage. It presents organisations with an overview of problems that exist throughout the organisation’s structure. The IT administrator of a company exports all or selected email folders from the email server. The user is not aware of this collection. The emails folders are then loaded into an eDiscovery platform. The Electronic Discovery workflow needs to be modified specifically for DLP.
Some of the processing and analytics functions will include:
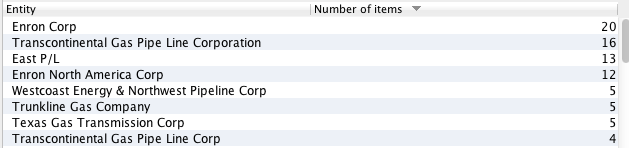
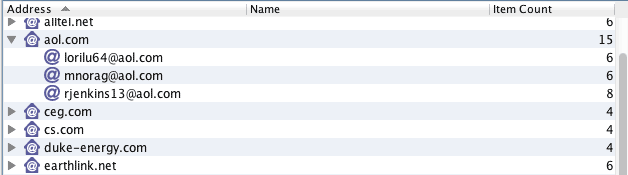
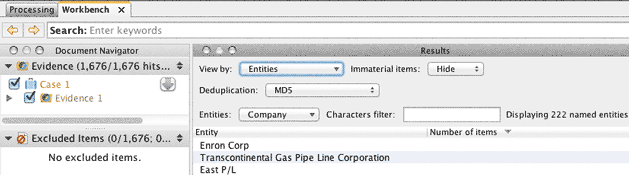
These methods are further bolstered by the ability to identify and “pull” certain relevant and irrelevant text within the documents themselves. This makes use of the powerful and modern textual analytics technology. In the past, processing terabytes of data was time consuming and expensive task. Today, using eDiscovery technology for Data Leak Protection has become a reality.
For organisations that concerned with the security of their information, Elvidence offers an effective “health check”. So, potential or ongoing threats can be identified and dealt with before they cost your organisation a great deal of time and money.